Protect Your PDFs: A Comprehensive Guide to PDF Security Features
Understanding the Importance of PDF Security
Did you know that a seemingly harmless PDF could be a gateway for malicious attacks? Protecting your PDF documents is more critical than ever in today's digital landscape.
- Protect sensitive information: PDFs often contain financial records, personal data, and confidential business plans. PDF security measures prevent unauthorized access, keeping this information safe. For instance, healthcare providers use secure PDFs to protect patient medical records, complying with HIPAA regulations.
- Prevent unauthorized viewing, copying, or modification: Security features can restrict who can open, edit, or print a PDF. This is crucial in industries like finance, where contracts and statements need to remain unaltered.
- Maintain document integrity and authenticity: Digital signatures and certificates ensure that a PDF hasn't been tampered with and confirm its origin. This is vital for legal documents and official records.
- Compliance with data protection regulations: PDF security helps organizations meet requirements like gdpr, ccpa, and HIPAA. For example, redaction tools can remove sensitive information from PDFs to comply with privacy laws.
- Unauthorized viewing or copying of content: Without proper security, anyone can access and copy sensitive information. This risk is mitigated by using permissions passwords, which restrict copying and printing, as discussed in the "Password Protection" section.
- Malicious modification of document content: Attackers can alter PDFs to spread misinformation or commit fraud. Keeping your PDF reader software updated, as detailed in the "Other Important PDF Security Considerations" section, helps prevent the exploitation of vulnerabilities that could lead to such modifications.
- Printing of confidential documents: Unauthorized printing can lead to data leaks and compliance violations. Permissions passwords, explained in the "Password Protection" section, can prevent this.
- Exploitation of vulnerabilities in PDF readers: Outdated or vulnerable PDF readers can be exploited to install malware. This risk is mitigated by keeping your PDF reader software updated, as discussed in the "Other Important PDF Security Considerations" section.
- Data breaches and compliance violations: Security breaches can result in significant financial and reputational damage. Implementing the security features discussed throughout this guide helps prevent these breaches.
PDF security features offer a range of tools to protect PDF documents. Adobe Acrobat provides advanced security features to keep your work as safe as possible.
- Customization: These features can be tailored to meet specific security needs, from simple password protection to advanced encryption.
- Comprehensive Protection: Effective PDF security requires a combination of technical measures and user awareness, ensuring all bases are covered.
Understanding the importance of PDF security is the first step toward safeguarding your valuable information; the next section will explore password protection, a fundamental PDF security feature.
Password Protection: Limiting Access to Your PDFs
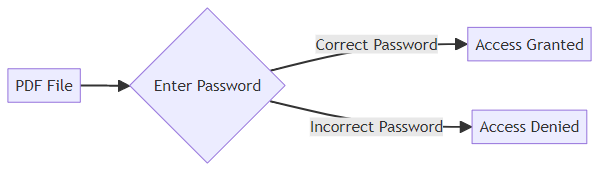
Password protection is like putting a digital lock on your valuable documents. It's one of the most straightforward ways to control who can access your PDFs.
An open password requires users to enter a password before they can even view the PDF. This is your first line of defense.
- It's a basic access control measure. Imagine a law firm securing sensitive client briefs with a password to prevent unauthorized eyes from reading them.
- Open passwords work best for documents with moderate sensitivity. Think internal reports, drafts, or shared documents within a team.
- For enhanced security, always choose a strong, unique password. Avoid easily guessable words or phrases.
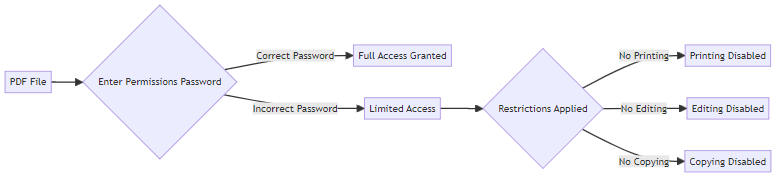
A permissions password goes a step further. Even if someone can open the PDF, you control what they can do with it.
- This type of password restricts actions like printing, editing, or copying content. A design firm might use a permissions password to prevent clients from altering design proposals before final approval.
- This is ideal for protecting intellectual property or confidential information. Educational institutions can prevent students from copying exam papers.
- The permissions password offers granular control over document usage. You decide exactly what actions are allowed.
Password protection is a great start, but remember that it's just one piece of the puzzle. For comprehensive security, consider combining it with other methods like digital signatures and encryption, as noted earlier.
Moving on, let's explore how to control printing, editing, and copying within your PDFs using permissions.
Encryption: Securing PDF Content with Algorithms
Did you know that encryption is like a digital vault for your PDFs, protecting sensitive information from prying eyes? It transforms readable text into an unreadable format, ensuring only authorized users can access the content.
Encryption transforms PDF content into an unreadable format. This scrambled data is only decipherable with the correct decryption key.
AES (Advanced Encryption Standard) is a modern and secure algorithm. It's widely used due to its strong protection capabilities. Adobe Acrobat, as mentioned earlier, uses advanced security features, which often include AES encryption.
RC4 is an older algorithm, generally considered less secure. While still functional, it's more vulnerable to attacks compared to AES. This is because RC4's keystream can exhibit statistical biases, making it susceptible to certain cryptanalytic attacks that can reveal patterns in the encrypted data.
Choose the strongest encryption algorithm supported by your PDF software and recipients' readers. This ensures maximum security without compatibility issues.
Encryption prevents unauthorized access to content, even if the PDF is intercepted. Think of it as scrambling a message so that only someone with the right code can read it.
It provides a strong layer of security for highly sensitive information. For example, a financial institution might encrypt PDF statements to protect customer data.
Requires a decryption key (password) to access the content. Without the correct key, the PDF remains unreadable, safeguarding the information within.
It's essential for compliance with strict data protection regulations. Encryption helps organizations meet standards like gdpr and HIPAA by securing sensitive data.
For instance, lawyers can secure confidential legal documents, and healthcare providers can protect patient records. Encryption, combined with password protection, offers a robust defense against unauthorized access.
As you consider these robust methods, digital signatures provide a way to ensure authenticity; we'll cover this in the next section.
Digital Signatures: Verifying Authenticity and Integrity
Did you know digital signatures are like a notary for your PDFs, ensuring they're authentic and haven't been tampered with? They provide a high level of trust in electronic documents.
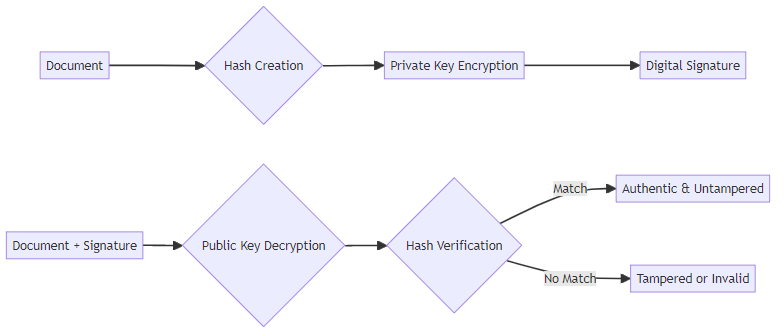
- A digital signature is an electronic, encrypted stamp of authentication. Think of it as a tamper-proof seal that guarantees the document's origin and integrity.
- It verifies the identity of the signer and ensures the document hasn't been altered since it was signed. This is crucial for legal contracts and official records.
- Digital signatures use public-key cryptography to create a unique signature. This involves a private key for signing and a public key for verification. When you sign a document with your private key, a unique digital fingerprint (the signature) is created. Anyone can then use your public key to verify that this fingerprint matches the document, confirming both your identity and that the document hasn't been altered.
- They provide non-repudiation, meaning the signer cannot deny their signature. This is essential in legally binding agreements, as even Adobe Acrobat uses digital signatures to keep your work safe as possible.
Digital signatures ensure document authenticity and integrity. They provide confidence that the document is genuine and hasn't been modified.
They provide legal validity and enforceability to electronic documents. This is crucial for contracts, agreements, and other legally binding documents.
They streamline document workflows and reduce paper usage. Digital signatures eliminate the need for physical signatures and paper-based processes.
They enhance security and trust in electronic transactions. Digital signatures provide a secure way to verify the identities of parties involved in a transaction.
Implementing digital signatures requires a digital certificate from a trusted Certificate Authority (CA). This certificate verifies the signer's identity.
PDF software provides tools to apply and validate digital signatures. This makes it easy to sign and verify documents electronically.
Signatures can be customized with visual representations (e.g., name, date, logo). This adds a personal touch and makes the signature more recognizable.
It's important to regularly update your digital certificates to maintain security. Expired certificates can invalidate signatures.
As you can see, digital signatures are a powerful tool for verifying authenticity, but what happens when you need to control who can see certain parts of your PDF? The next section will explore redaction tools.
Redaction: Permanently Removing Sensitive Information
Sensitive information lurking in your PDFs? Redaction offers a powerful way to scrub it clean, ensuring confidentiality.
Redaction permanently removes sensitive text and images from a PDF. Unlike simply hiding content, redaction makes it irretrievable. Think of it as using a digital black marker that can't be erased.
- Redaction is essential for complying with privacy regulations and protecting confidential data. For example, legal firms redact client information from court documents before public filing.
- Use redaction tools carefully to avoid accidentally removing important information. Always double-check your selections before applying redaction.
- Government agencies use redaction to protect classified information in publicly released documents.
Proper redaction ensures sensitive data is truly gone, not just hidden from view.
- Use dedicated redaction tools in PDF software. Examples include Adobe Acrobat Pro, Foxit PhantomPDF, and Nitro Pro. These tools are designed to permanently remove content.
- Mark sensitive content for redaction. Carefully select the text or images you want to remove.
- Apply the redaction to permanently remove the content. This process overwrites the selected areas with black bars or other solid blocks.
- Verify that the redacted content is completely removed from the PDF. Open the PDF in different viewers to ensure the redaction is consistent.
- Inspect the PDF to ensure no metadata reveals sensitive information. Metadata can sometimes contain traces of the redacted content.
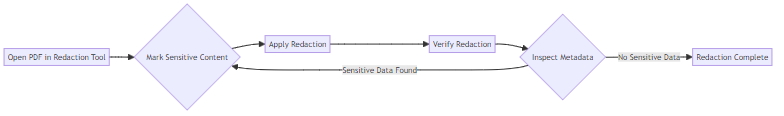
Following these steps ensures your PDFs are secure and compliant.
Now that you know how to permanently remove sensitive information, let's explore other crucial aspects of PDF security, such as managing JavaScript, attachments, and software updates.
Other Important PDF Security Considerations
Did you know that seemingly minor oversights in PDF handling can create major security gaps? Let's explore some often-overlooked aspects of PDF security to ensure comprehensive protection.
JavaScript can make PDFs interactive, but it also opens doors to potential risks. Malicious scripts embedded in PDFs can exploit vulnerabilities in PDF readers.
- If JavaScript isn't essential for your workflows, disable JavaScript execution in your PDF reader. This simple step significantly reduces the attack surface.
- Exercise caution when opening PDFs from untrusted sources. A seemingly harmless document could contain malicious code.
- Keep your PDF reader software up to date. Updates frequently include patches for newly discovered JavaScript-related vulnerabilities, as Adobe Acrobat frequently rolls out security updates.
PDFs often contain attachments, which can be another source of security vulnerabilities. Attachments might harbor malware or other harmful content.
- Always scan attachments for malware before opening them. Use a reputable antivirus program to check for threats.
- If attachments are not a necessary feature, restrict the ability to add or open them. This minimizes the risk of malicious files entering your system.
- Educate users about the risks of opening attachments from unknown sources. Awareness is crucial in preventing security breaches.
PDF readers and editors are common targets for attackers. Regular updates are essential for maintaining a secure environment.
- Install security updates promptly to patch vulnerabilities. Software vendors release updates to address newly discovered security flaws.
- Enable automatic updates whenever possible. This ensures you're always running the latest, most secure version of your PDF software.
- While not a PDF-specific feature, regularly scanning your system for malware is a crucial layer of defense that complements your PDF security measures. This helps detect and remove any malicious software that may have slipped through other defenses.
Taking these additional PDF security considerations seriously will significantly bolster your overall defense strategy. Looking ahead, the next section provides a summary of the key steps you can take to secure your PDFs.
Best Practices for PDF Security
Did you know that a single lapse in PDF security can expose your organization to significant risks? Implementing best practices is crucial to defend against potential threats and ensure data protection.
Establishing a clear PDF security policy is the foundation of any robust protection strategy. This policy should outline specific guidelines for securing PDF documents, ensuring everyone in your organization understands their responsibilities.
- Define password requirements, specifying the minimum length, complexity, and frequency of password changes. For instance, require a mix of upper and lowercase letters, numbers, and symbols.
- Set encryption standards to determine when and how PDFs should be encrypted, using algorithms like AES.
- Establish clear redaction procedures to permanently remove sensitive information from documents before sharing them.
- Train employees on these best practices and regularly update the policy to address emerging threats.
Selecting the right PDF software is essential for implementing your security policy effectively. Not all PDF tools offer the same level of protection, so it's important to choose solutions with robust features.
- Look for software that provides strong encryption, digital signature support, and reliable redaction capabilities.
- Consider the vendor's security track record and how often they release updates to patch vulnerabilities.
- Ensure the software is compatible with your existing IT infrastructure and can be easily integrated into your workflows.
- Adobe Acrobat emphasizes its robust encryption and digital signature capabilities to ensure document security.
Even the most advanced security tools are ineffective if users aren't aware of the risks. Raising awareness and training employees is crucial for preventing security breaches.
- Educate users about phishing attacks and how to identify malicious PDFs. Teach them to be cautious when opening documents from untrusted sources.
- Emphasize the importance of strong passwords and secure file sharing practices. Encourage the use of password managers and secure file transfer protocols.
- Promote a culture of security awareness within your organization, where everyone understands their role in protecting sensitive information.
- Adobe Acrobat's resources often highlight the critical role of document security in maintaining trust and compliance.
By developing a comprehensive security policy, choosing the right tools, and educating users, you can create a strong defense against PDF-related security threats. Taking these steps will help you protect sensitive information and maintain compliance with data protection regulations.